As organizations strive to deliver always-on access to applications users, it can be challenging to provide authorized access while simultaneously protecting against cyber-attacks. To address these challenges, two novel solutions combine the power of application delivery controllers (ADCs) with web access management (WAM) and database security technologies.
Letting the Good Guys In
Identity and access management solutions seek to provide contextual access to the right users at the right time, but also to protect corporate resources. Figure 1 shows a typical architecture.
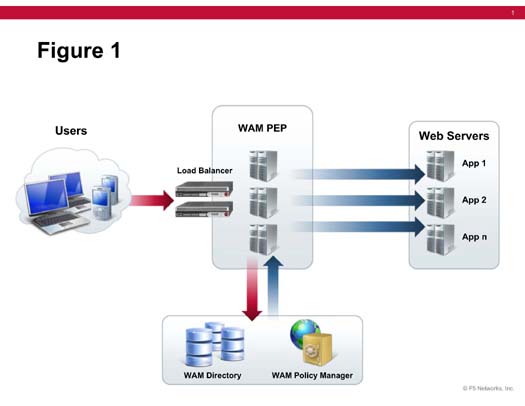
Figure 1. Typical Identity and Access Management Architecture
When a user initially attempts to access a web application, that request is intercepted by a software agent that is deployed on a proxy server. These agents serve as policy enforcement points (PEPs) to protect and enable access to applications. For high availability, each application requires pair of agents that are load-balanced. If web access management is required for hundreds or thousands of applications, it can be very costly to implement and maintain. This architecture does not scale easily.
Figure 2 shows an alternative. In this case, the ADC serves as both a load-balancer and WAM PEP. This eliminates the need to deploy and maintain agents on proxy servers, thus simplifying the architecture and dramatically reducing costs.
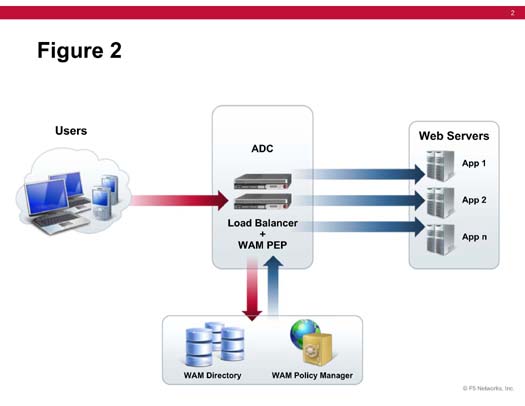
Figure 2. ADC and WAM Architecture
Keeping the Bad Guys Out
A database is the primary repository and for an enterprise’s critical data—and protecting that database is crucial. As more application traffic moves over the web, sensitive data is exposed to new security vulnerabilities and attacks. Standalone technologies that protect against web or database attacks are available, but their disconnection from one another means they lack context. Organizations need an end-to-end web application and database security solution to protect their data.
When a database firewall receives a request for access, typically it comes from the web server tier in front of the database. Because it is coming from the web server, the request looks legitimate. Malicious hackers take advantage of this trusted status by attempting a SQL injection attack to fool the database into divulging sensitive information. A database firewall, which protects against such an attack, does not have the visibility to gather information such as host name, user name, client IP, and browser. While it can see that a particular SQL query is invalid, it cannot decipher who made the request.
An ADC web application firewall (WAF) on the other hand gathers user-side information so it can base policy decisions on the user’s context. A WAF monitors every request and response from the browser to the web application and consults a policy to determine whether to allow the action and data. It uses information like user, session, cookie, and other contextual data to decide if the request is valid. WAFs are primarily focused on HTTP attacks and do a great job of thwarting that type of malicious traffic. Although they can also protect against SQL injection attacks, given the complexity of detecting such attacks in the web application tier, WAFs are not a fool-proof SQL injection prevention solution.
The integration of a WAF and a database firewall provides protection at both the web application and database tiers. Figure 3 shows the architecture of the solution.
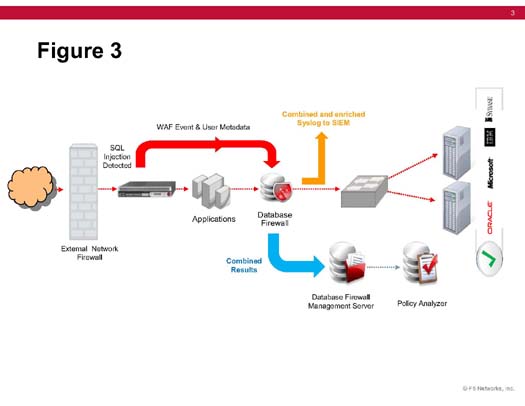
Figure 3. Architecture of ADC WAF and Database Firewall Solution
The power of a WAF and a database firewall working together is in the consolidated reporting of attacks, and the ability to set policy at the web application layer, which is coordinated at the database layer. Thus, an enterprise’s database is protected by a layered, defense-in-depth architecture, backed with the contextual information required to make intelligent decisions about database security incidents. It enables enterprises to adapt quickly to changing threats and provides the logging and reporting needed to meet auditing and compliance regulations.
Conclusion
Providing access to applications and data while simultaneously protecting against cyber-attacks is challenging. Combining ADCs with web access management and database firewall technologies delivers streamlined and cost-effective access management in addition to providing contextual, layered security in the data center.